

Smart solutions for Maximum PC UPTIME
- The ability to solve many issues/problems with a
quick recovery reboot! - The ability to easily revert back from Ransomware and wiping attacks -
at how fast your computer reboots! LockBit ransomware takes as little as five minutes to deploy/encrypt your data. Our service easily reverts encryption and gives you back full access to your data
-within minutes! - Blue Screen of Death (B.S.O.D.)
Is the in-ability to boot up windows. We provide you
with the ability to simply reboot, and boot up normal! - Our effective solutions are designed for PC Resiliency, Continuity, Security, Disaster Recovery, Ransomware,
and Data Shielding from the start! - Virus break out -
instantly perform a full removal, just
by doing a system restart. We provide you with the ability to simply reboot, tap a few keys, and boot up normal! - Baseline security starting out with ransomware and
anti-wipe data shielding for your data, with the ability
to perform PC restore -upon reboot! - Our service is designed to lower IT costs. In fact, approximately near 70% of support costs are lessened with our baseline service alone -
an immediate ROI!
A Truly Proactive Approach
We think outside the box when it comes to your service
and support. We strive upon innovation and work close with partners to execute further and become more
precise when it comes to delivering
Friendly quality support & service
Partnering with us provides you with the feeling of your personal tech in your pocket.
Overlay Protection
When an application tries to modify a protected file, it
gets redirected and the file modification is stored on an overlay. Keeping the original file intact.
Contact us for full information and how you can get started with true protection for your workstations and servers.
No more Ransom. Call today 301.498.1515

Why backup struggles with ransomware
Ransomware has become the scourge of many businesses and is
likely not to disappear as a threat anytime soon. If anything,
ransomware is on the rise, as evidenced by the Cybersecurity and Infrastructure Security Agency (CISA), which observed an increase
in ransomware attacks across the world so far this year. That proves
to be troubling news as many organizations have recently adopted
work-



Traditional backup solutions often are not effective when dealing
with a ransomware infestation simply because backup was only designed to recover from file deletion, corruption or catastrophic hardware failure.
However, in the case of ransomware, backup has little ability to
remove threats or clean up any infected system.
Typically administrators will need to format a computer and create
a clean environment before restoring data from a backup. This is something business owners would only discover after spending numerous hours on restoring a backup. This was proved out by
some ad-
Ad-
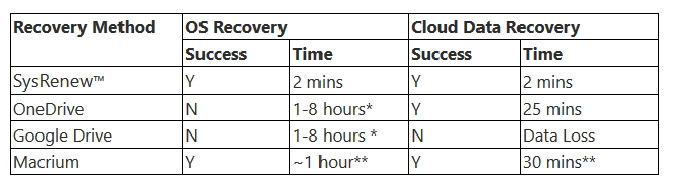
Testing was performed on a virtual machine environment running Windows 10, with files synced to both Google Drive and Microsoft OneDrive. A ransomware attack was conducted using BadRabbit
and Unlock92, two pieces of ransomware that can be found in the
wild, and are often used as a starting point for many cyber criminals.
Testing methodology consisted of starting with a restored VM snapshot (to set up the basic system for testing), executing
the ransomware, then using a recovery method to restore the
OS and the damaged data files. The results of the tests exemplify
the differences between the different recovery methods and offer
a practical assessment of how SysRenew™ can benefit a business
that has suffered a ransomware attack.
* Based on Microsoft’s time of one hour to install Windows, plus any additional time to install patches and applications and set up email and other custom settings required by the user.
** Macrium requires a reinstallation of the OS and the Macrium software before it can do a full restore on the original OS and data from the backup image. In the latter case, it took 30 mins.
 Learn more about SysRenew™
Learn more about SysRenew™
Proactive cybersecurity
Instant recovery technology: There’s a big difference between a cyberattack and a cyber breach. While ransomware breaches may not be one hundred percent preventable, they can be reversible. We can’t always prevent a cyberattack, but we can prevent data loss from a breach. This is where instant recovery comes in and is a critical component of our multi-
A system that recovers data and operating systems within minutes, no matter how much was encrypted, saves valuable time and money. An instant recovery system adds an overlay to files and operating systems as a protective barrier to prevent them from being modified by hackers. It relieves IT personnel from having to recover data from backup systems and manually re-
Every organization with digital assets should have a multi-


©ComPerSol Computer Performance Solutions 2023|All rights reserved|Pricing subject to change and does not include taxes and/or S&H|SysRenew™ is a trademark of Compersol, Computer Performance Solutions 2013-